 CONTACT US
CONTACT US

ORIGINAL ARTICLE PUBLISHED AUGUST 2019 IN THE PRAGMATIC
Of course, not all your company knowledge is appropriate to make public. You're privy to proprietary information that you could unintentionally expose, compromising your company's work and eroding its competitive advantage. Are you mindful of the valuable information you give away?
Protecting your company's information — practicing counterintelligence — presents an increasing challenge. Despite the opportunity cost, counterintelligence and data-leakage assessments remain inadequately addressed at many corporations. Further, most attention focuses on cybersecurity/digital threats, but analog/human data leakage is more widespread and harder to prevent. Most U.S. C-suite leaders (84%) identified employee negligence as their biggest information security risk, according to Shred-It's 2018 State of the Industry: Information Security report.
Competitive-intelligence collection that targets your company can have real business consequences. To understand your role in protecting your company's information, consider the relationship among proprietary information, competitive intelligence and counterintelligence.
Proprietary information is material deemed sensitive to your organization or company. It's information that shouldn't be shared externally without a solid business reason — and only then when following company, legal and regulatory requirements. Examples include:
Competitive intelligence is like assembling a puzzle that starts with seemingly unrelated puzzle pieces. As you slide more pieces into place, a cohesive picture emerges. More images emerge with each newly fitting piece, and you become confident that you're on the right track.
Similarly, skilled intelligence gatherers can amass many individual data points about a company like yours. They assemble and triangulate these points until an accurate understanding of nonpublic, often proprietary aspects of the company emerge. Each data point that better fills in a bigger picture can potentially harm your company. For instance, a colleague in a public coffee shop who comments on the details of an impending company downsizing may unknowingly be overheard by a competitor who combines it with other, related data. Now your competitor can better anticipate your company's confidential restructuring plans and related implications.
Companies that compete against yours seek a competitive edge. Building a deep enough understanding of your company can help them outperform you, preempt or neutralize your initiatives, emulate your successes and take advantage of your weaknesses. Your competitors can assemble this type of intelligence through activities such as:
Once you're aware of the risky signs and locations, you're ready to put your knowledge into action. Consider these two scenarios that provide opportunities to practice responsible counterintelligence.
When you receive unsolicited external contacts by phone or email (e.g. asking you to participate in a suvey about a company-related topic), it's critical to authenticate the inquirer's identity, and, in the case of surveys, demand the identity of the survey sponsor.
Before responding, think through the information you can share safely. Next, you may need to take one of several precautionary measures, ranging from politely disengaging the caller to initiating an internal process that leads to a formal cease-and-desist notice from your comapny's legal team.
In intelligence gathering-rich environments like industry conferences, competitors come seeking information ot fill in important puzzle-pieces about your company. In these situations, you can take several precautions:
Counterintelligence is the practice of managing the range of intelligence-gathering activities directed at your company. And the heavy external-communication nature of your role makes counterintelligence especially important. You undermine your company's success when you are unaware of the value of the proprietary information you possess and don't actively manage external access to it.
You and your peers can execute sound counterintelligence by knowing the signs of potential intelligence-targeting activity, becoming aware of risky situations and knowing the protective steps to take.
Common signs can indicate someone is targeting your company for competitive-intelligence collection. Use caution with inquirers conducting activities such as collecting information for a survey or undisclosed client, or fact-checking for a publication or presentation. In particular, watch for inquiries from people in roles such as:
Legal or otherwise, intelligence-gathering techniques continue to grow in sophistication and volume. In the end, the burden of proof lies on the responder (or the unaware leaker), not on the inquiring individual. Ultimately, it's your responsibility to protect your company's information and its competitive edge.
For example, you run a higher risk of exposing proprietary information in certain locations. Among others, be alert to places such as:
But you don't carry this responsibility alone. Counterintelligence requires support at the company level: A critical protective measure should be to have regular reminders from senior management or legal to reinforce what constitutes confidential, proprietary information that should never be shared. It's equally crucial to sensitize nonemployees (e.g., channel partners, solution providers) to the severe bottom-line consequences that leaking sensitive data can wreak.
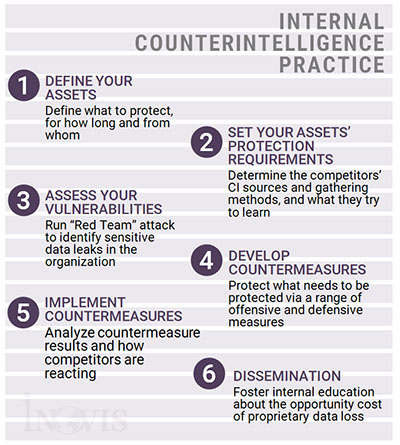
Your company leadership also should initiate and maintain corporate expectations for awareness of signals that may constitute a potential attack — and direction about how to act on them. Figure 1 illustrates the best practices for fostering an internal culture of counterintelligence.
It also can be helpful to collaborate with a third-party partner to train cross-functional teams on counterintelligence-awareness programs, facilitate role-playing with data-elicitation techniques or stage a "red team attack to identify areas of data leakage in your organization. Then, educate affected parties about how to prevent future leaks.
And remember: Balance is important. There's no need to go as far as former Intel CEO Andy Grove's famous corporate mantra, "Only the paranoid survive. But do advocate for making all cross-functional teams aware of intelligence-targeting risks and the means to defend against them. A robust awareness and training program across the organization coupled with a report and follow-up process for flagged counterintelligence events is mission-critical to protect your company's proprietary assets.
At its most effective, counterintelligence includes fostering a culture of mindfulness across your organization and company. It's true that your role as a product marketer or product manager gives you unique exposure to risky intelligence situations. But it also gives you an opportunity to protect your company — and remind your colleagues to do the same. Responsible gatekeeping of your company's proprietary information starts with you. Use your influence to ensure it doesn't stop there.

Marc Limacher started INOVIS in 1992 as a boutique primary CI specialty firm in Palo Alto, CA, specializing in the pharma/medtech, digital health and IT industries.
